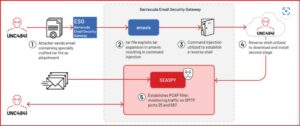
The hackers used a security hole in a popular email security appliance to infiltrate the networks of numerous public and private organizations worldwide.
Approximately one-third of the targeted entities were government agencies, including foreign ministries. Carmakal, described the campaign as the most extensive cyber espionage activity attributed to a China-linked group since the mass exploitation of Microsoft Exchange earlier in 2021.
The hackers used SALTWATER aka Seaspy malware. They sent malicious file attachments via email to gain unauthorized access to targeted organizations’ devices and data. SALTWATER can upload or download arbitrary files, execute commands, and has proxy and tunneling capabilities.
The report reveals that the attacks predominantly targeted organizations in the Americas, accounting for 55% of the victims. Asia Pacific accounted for 22%, while Europe, the Middle East, and Africa comprised 24% of the targeted entities.
Foreign ministries in Southeast Asia, foreign trade offices, and academic organizations in Taiwan and Hong Kong were also affected. Mandiant’s investigation linked the attacks to Chinese-linked hackers, who targeted public agencies, schools, and high-value information targets across the globe.


