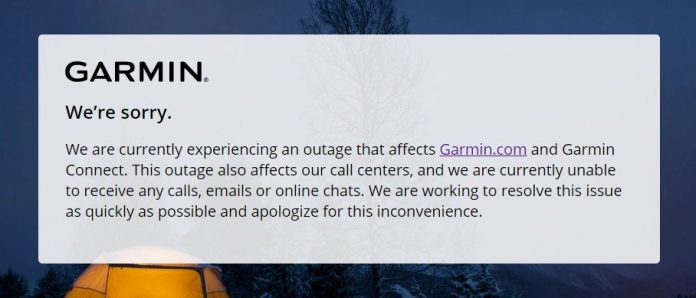
American multinational GPS and wearable device maker Garmin Ltd. shut down some of its connected services and call centers on Thursday following what the company called a worldwide outage, widely thought to have been caused by a WastedLocker ransomware attack.
In addition to consumer wearables and sportswear, flyGarmin was also down on Thursday. This is Garmin’s web service that supports the company’s line of aviation navigational equipment.
It is being widely reported that the cybercriminals, Evil Corp, are demanding $10 million dollars. On Sunday, July 26, there was no indication of whether or not the ransom will be paid. All systems still appeared to be locked down at Garmin.
While Garmin didn’t disclose it in their outage alerts, it was reported on the Bleeping Computer website that multiple flyGarmin services used by aircraft pilots also went down.
WastedLocker ransomware attack shuts down Garmin
Early reports state that the attack started in Taiwan. iThome published a report about a ‘virus’ attack affecting the company’s internal IT servers and databases.