Kelly Warner Law Firm Blames USA Herald for Arizona Bar Investigation
5/17/17 Based on the information released in The Washington Post article on 5/17/17, the USA Herald publishes another in-depth article that…
By – USA HeraldAaron Kelly Law Firm Resorts To Attacking Former Client Again On KellyWarnerLaw.com – Pattern Recognized
Professor Volokh thereafter filed a bar complaint against Dan Warner with the Arizona Bar. This eventually led the ABA to…
By – Jeff WattersonArizona Bar Opens Investigation on Attorney Aaron Kelly
Volokh, as part of his investigative work, had a private investigator research the defendants in some of theallegedly fraudulent…
By – Paul O'NealKanye West’s Malibu Mansion Trial Takes Dramatic Turn in Court
Bianca Censori Testified a Day Earlier Ye’s testimony followed an earlier appearance by his wife, Bianca Censori, who took the…
By – Rihem AkkoucheKuwait Cuts Oil Production as Gulf Tanker Threats Disrupt Global Energy Flow
Risk of $100 Oil Looms Analysts warn the situation could deteriorate quickly. Kaneva said Gulf producers could exhaust available storage…
By – Rihem AkkoucheOpenAI’s Caitlin Kalinowski Resigns Over Controversial Pentagon AI Agreement
Public Reaction and App Store Shifts The controversy has also rippled across the consumer tech landscape. Following the announcement of…
By – Rihem AkkoucheTornadoes Damage in Michigan Leaves Multiple Dead as Severe Storms Sweep Across U.S.
Tornado Also Claims Lives in Oklahoma The storm system did not stop at Michigan’s borders. In Oklahoma, officials said a…
By – Rihem AkkoucheUS Draft AI Chip Sales Rules Could Reshape Global Tech Power Balance
A Shift Away From Biden’s AI Strategy The new approach marks the administration’s most significant move toward a global semiconductor…
By – Rachel MooreSix Flags Amusement Parks Sale Signals Major Shake-Up in Theme Park Industry
Clues From Trademark Filings Earlier signals of the shift surfaced in January 2025, when trademark filings reviewed by PEOPLE revealed…
By – Rachel MooreKanye West’s Malibu Mansion Trial Takes Dramatic Turn in Court
Bianca Censori Testified a Day Earlier Ye’s testimony followed an earlier appearance by his wife, Bianca Censori, who took the…
By – Rihem AkkoucheKuwait Cuts Oil Production as Gulf Tanker Threats Disrupt Global Energy Flow
Risk of $100 Oil Looms Analysts warn the situation could deteriorate quickly. Kaneva said Gulf producers could exhaust available storage…
By – Rihem AkkoucheOpenAI’s Caitlin Kalinowski Resigns Over Controversial Pentagon AI Agreement
Public Reaction and App Store Shifts The controversy has also rippled across the consumer tech landscape. Following the announcement of…
By – Rihem AkkoucheTornadoes Damage in Michigan Leaves Multiple Dead as Severe Storms Sweep Across U.S.
Tornado Also Claims Lives in Oklahoma The storm system did not stop at Michigan’s borders. In Oklahoma, officials said a…
By – Rihem AkkoucheUS Draft AI Chip Sales Rules Could Reshape Global Tech Power Balance
A Shift Away From Biden’s AI Strategy The new approach marks the administration’s most significant move toward a global semiconductor…
By – Rachel MooreSix Flags Amusement Parks Sale Signals Major Shake-Up in Theme Park Industry
Clues From Trademark Filings Earlier signals of the shift surfaced in January 2025, when trademark filings reviewed by PEOPLE revealed…
By – Rachel MooreKanye West’s Malibu Mansion Trial Takes Dramatic Turn in Court
Bianca Censori Testified a Day Earlier Ye’s testimony followed an earlier appearance by his wife, Bianca Censori, who took the…
By – Rihem AkkoucheKuwait Cuts Oil Production as Gulf Tanker Threats Disrupt Global Energy Flow
Risk of $100 Oil Looms Analysts warn the situation could deteriorate quickly. Kaneva said Gulf producers could exhaust available storage…
By – Rihem AkkoucheOpenAI’s Caitlin Kalinowski Resigns Over Controversial Pentagon AI Agreement
Public Reaction and App Store Shifts The controversy has also rippled across the consumer tech landscape. Following the announcement of…
By – Rihem AkkoucheTornadoes Damage in Michigan Leaves Multiple Dead as Severe Storms Sweep Across U.S.
Tornado Also Claims Lives in Oklahoma The storm system did not stop at Michigan’s borders. In Oklahoma, officials said a…
By – Rihem AkkoucheUS Draft AI Chip Sales Rules Could Reshape Global Tech Power Balance
A Shift Away From Biden’s AI Strategy The new approach marks the administration’s most significant move toward a global semiconductor…
By – Rachel MooreSix Flags Amusement Parks Sale Signals Major Shake-Up in Theme Park Industry
Clues From Trademark Filings Earlier signals of the shift surfaced in January 2025, when trademark filings reviewed by PEOPLE revealed…
By – Rachel MooreU.S. And Israel Launch Major Strikes On Iran — What It Means For America
Continuation of military strikes if Iran persists in retaliatory attacks. Diplomacy or ceasefire negotiations if international pressure increases. A broader…
By – Samuel LopezU.S. Court of Appeals for the Ninth Circuit Overturns $8M Asbestos Verdict Against BNSF Railway Co.
BNSF declined to comment on the decision. Judges Consuelo M. Callahan, Morgan B. Christen and Andrew D. Hurwitz sat on…
By – Tyler BrooksMissing DNA Evidence May Limit Investigation Into Nancy Guthrie Case, Sources Suggest
Representatives from FamilyTreeDNA emphasized that the company operates under strict privacy standards and does not directly conduct investigative work for…
By – Ahmed BoughallebGrand Theft Auto 6 Targets November 2026 Launch as Price Leak Fuels $100 Debate
After years of speculation, teaser trailers and headline-making leaks, Grand Theft Auto VI now has a confirmed global release date:…
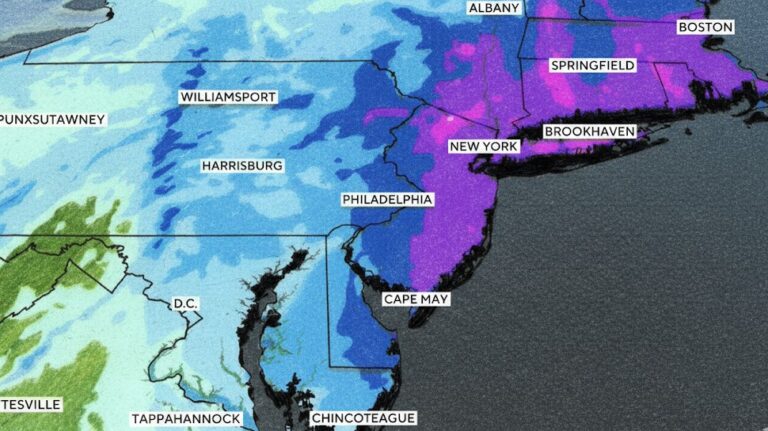
By – Ahmed Boughalleb40 Million Under Blizzard Warnings as Major Winter Storm Threatens U.S. East Coast
“This will be something the likes of which we have not seen in years,” Hochul said. She warned that residents…
By – Tyler BrooksViolence Erupts Across Mexico After Cartel Leader “El Mencho” Killed in Military Raid, Triggering Roadblocks, Transport Disruptions, and Security Alert Across Several States
Several airlines adjusted schedules due to the security situation. Air Canada suspended flights to Puerto Vallarta because of ongoing safety…
By – Ahmed BoughallebKanye West’s Malibu Mansion Trial Takes Dramatic Turn in Court
Bianca Censori Testified a Day Earlier Ye’s testimony followed an earlier appearance by his wife, Bianca Censori, who took the…
By – Rihem AkkoucheKuwait Cuts Oil Production as Gulf Tanker Threats Disrupt Global Energy Flow
Risk of $100 Oil Looms Analysts warn the situation could deteriorate quickly. Kaneva said Gulf producers could exhaust available storage…
By – Rihem AkkoucheOpenAI’s Caitlin Kalinowski Resigns Over Controversial Pentagon AI Agreement
Public Reaction and App Store Shifts The controversy has also rippled across the consumer tech landscape. Following the announcement of…
By – Rihem AkkoucheTornadoes Damage in Michigan Leaves Multiple Dead as Severe Storms Sweep Across U.S.
Tornado Also Claims Lives in Oklahoma The storm system did not stop at Michigan’s borders. In Oklahoma, officials said a…
By – Rihem AkkoucheUS Draft AI Chip Sales Rules Could Reshape Global Tech Power Balance
A Shift Away From Biden’s AI Strategy The new approach marks the administration’s most significant move toward a global semiconductor…
By – Rachel MooreSix Flags Amusement Parks Sale Signals Major Shake-Up in Theme Park Industry
Clues From Trademark Filings Earlier signals of the shift surfaced in January 2025, when trademark filings reviewed by PEOPLE revealed…
By – Rachel MooreWhen The Files Are Finally Unsealed The Most Mind-Bending Truth May Not Be What We Expect
[USA HERALD] – There is a widespread assumption that if governments release their most highly classified files related to unidentified…
By – Samuel LopezCivil Rights Icon Rev. Jesse Jackson Dies at 84 As President Trump Issues Personal Tribute
Domestically, he applied sustained pressure on corporations to diversify their leadership ranks and invest in minority communities. He publicly challenged…
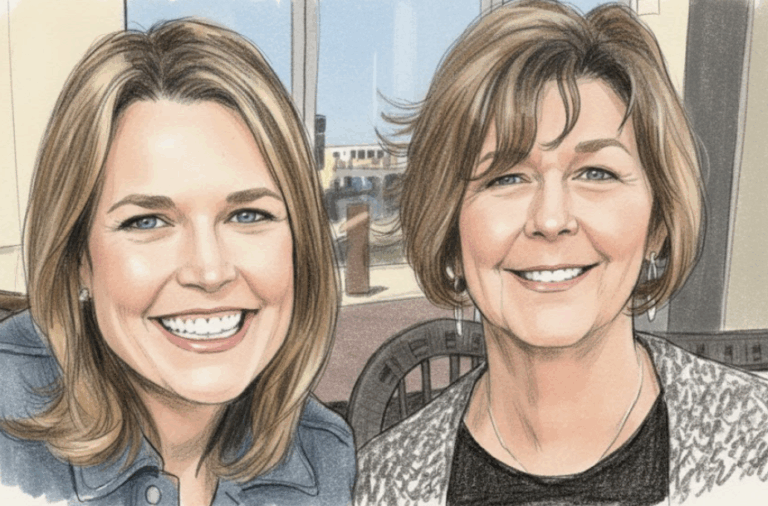
By – Samuel LopezClues to Savannah Guthrie Missing Mom’s Disappearance Found on Security System
Savannah Guthrie Concerned about Ongoing Investigation With the case entering its second week, investigators remain focused on integrating physical evidence…
By – Jackie AllenMike Tyson Urges Americans to ‘Eat Real Food’ in Emotional Super Bowl Ad Highlighting Health Risks
Boxing legend Mike Tyson is using his platform ahead of Super Bowl 60 to address a personal and national health…
By – Tyler BrooksDeadly “Death Cap” Mushrooms in California Cause Multiple Deaths and Liver Transplants Amid Rare Super Bloom
California health officials are warning the public after four deaths and three liver transplants linked to the highly toxic death…
By – Ahmed BoughallebFrom Migraines to Miracles: How Becca Valle Survived a Glioblastoma Diagnosis Against the Odds
Becca Valle, 41, thought her headaches were just migraines—until a sudden, unbearable pain revealed something far more serious. In September…
By – Tyler BrooksCadillac Names Inaugural Formula 1 Car MAC-26 in Tribute to Mario Andretti Ahead of 2026 Australian Grand Prix Debut
That persistence ultimately paid off, culminating in the green light for Cadillac’s 2026 entry. Leadership and Vision Team principal Graeme…
By – Ahmed BoughallebNorway Tops Medal Table After Day 13 at 2026 Winter Olympics as Team USA Surges Into Second Place
Upcoming Medal Events Medal competition continues Friday, February 20, with several key finals scheduled. Events awarding medals include: Women’s ski…
By – Ahmed BoughallebOlympic Science Explained: How Figure Skaters Spin at Blinding Speeds Without Getting Dizzy
By – Tyler Brooks
Olympic Villages Run Out of Condoms at 2026 Milan-Cortina Games
Condom supplies in the Olympic Villages at the 2026 Winter Games have been temporarily depleted, the Milan-Cortina organizing committee confirmed,…
By – Tyler BrooksArizona Authorities Escalate Search for Savannah Guthrie’s Mom to a Criminal Investigation
USA TODAY’s live coverage: https://www.usatoday.com Pima County Sheriff’s Office: https://www.pimasheriff.org NBC News reporting: https://www.nbcnews.com As the investigation continues, officials say…
By – Jackie AllenWhat is Aegosexuality?
This early classification, however, sparked significant criticism. Advocates argue that placing aegosexuality in this category not only misunderstood the experience…
By – Jackie AllenNo posts found.
No posts found.
 No comments yet. Be the first to comment!
No comments yet. Be the first to comment!